The Prequel Difference
Cybersecurity & Diligence
Prequel Solutions has made cybersecurity and its diligent recruitment process its highest priority, and therefore, it deserves a product named 3MFA —Three-Meeting Final Assessment.
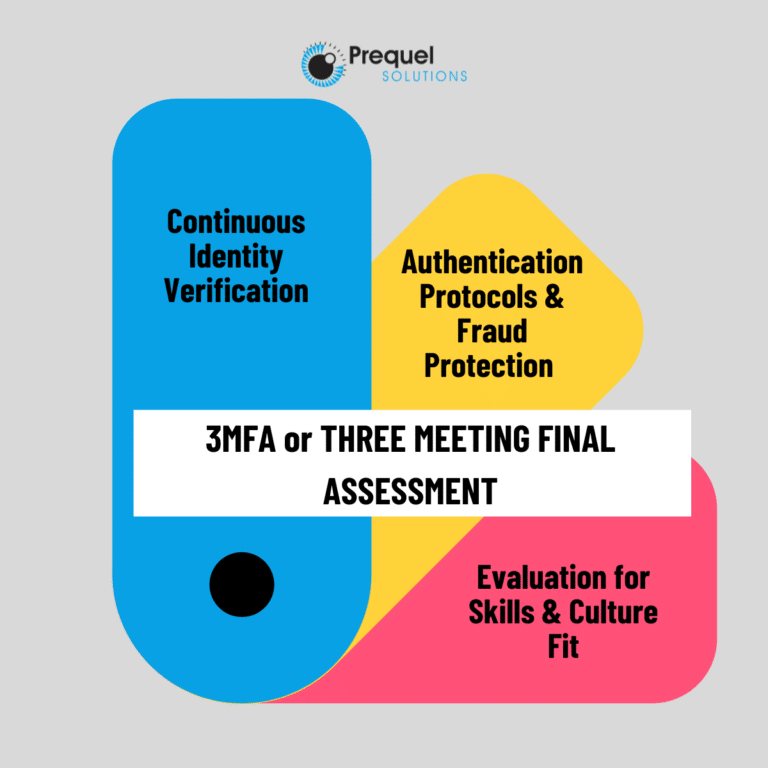
3MFA – Three Meeting Final Assessment
These three meeting assessment steps confirm the candidate’s real identity, background, and work history. We meet with the candidate three times, which protects against fraud and helps us stay ahead of AI-generated resumes and deepfake interviews.
In our 3MFA, we maintain consistent authentication protocols- confirm candidate identities by matching their appearance with official identification documents during real-time video interviews.
Our proprietary process helps us to assess skills, culture fit, and long-term success. Hiring the right person is too important to rely on just one interview or gut instinct. We go the extra mile so you have peace of mind.
Our rigorous vetting process ensures that every direct and contract hire we provide is proficient for the role, and real.
As recruitment fraud becomes increasingly complex, organizations need to implement robust candidate screening protocols. Companies that fail to establish comprehensive verification systems face significant challenges:
- bringing aboard individuals lacking the necessary qualifications
- squandering critical time and financial resources
- and potentially creating serious security vulnerabilities within their operations.
The evolving landscape of hiring deception demands a strategic and vigilant approach to candidate assessment. Without these protective measures, businesses risk reduced productivity and wasted onboarding investments and expose themselves to data breaches and other security compromises that could damage both operations and reputation.
Our 3MFA Process Includes:
Continuous Identity Verification
These three meeting assessment steps confirm the candidate’s real identity, background, and work history. We meet with the candidate three times, which protects against fraud and helps us stay ahead of AI-generated resumes and deepfake interviews.
Authentication Protocols & Fraud Protection
Consistent authentication protocols confirm candidate identities by matching their appearance with official identification documents during real-time video interviews.
Evaluation for Skills & Culture Fit
Our proprietary process saves you time and money and helps us assess skills, culture fit, and long-term success. Getting it right the first time is crucial to your company’s growth and success.